
Introduction
Cyberattack does not care about the sectors. As we see in our previous blog articles, attackers are breaching defenses with increasingly sophisticated techniques, exposing not just data, but also trust from the supermarket retailer sector in SPAR case to a daily cooking IoT appliance Thermomix case. This relentless evolution underscores a critical truth of the fact that no organization, regardless of its industry or perceived security, is immune.
In this blog article, we delve into the recent fashion brand cyber attack cases to examine the data breaches at Cartier, The North Face, and Victoria’s Secret. What can these high-profile incidents teach us about vulnerability, defense, and the continuing threat in the digital age?
What happened?
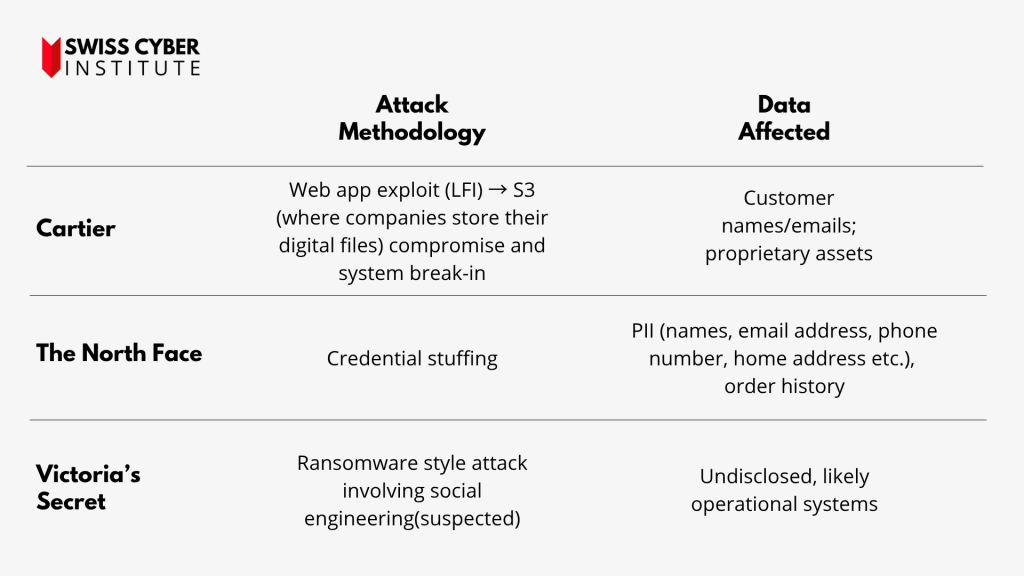
Cartier
In early June 2025, luxury jeweler Cartier confirmed a cyberattack that resulted in an “unauthorized party” gaining temporary access to their system. The compromised data included customer names, email addresses, and countries of residence. Crucially, Cartier emphasized that sensitive financial information, such as passwords, credit card details, or banking information, was not affected. The brand acted rapidly to contain the issue and engaged external cybersecurity experts, notifying relevant authorities. While the specific perpetrators remain unconfirmed, this incident underscores that even high-end brands holding valuable customer data are prime targets.
The North Face
Around April 2025, outdoor apparel giant The North Face disclosed a data breach affecting approximately 1,500 to 2,800 customer accounts. This attack was attributed to “credential stuffing,” a technique where cybercriminals use usernames and passwords stolen from other data breaches to gain unauthorized access to accounts where users have reused their credentials. The compromised information included names, email and shipping addresses, dates of birth, and telephone numbers. Similar to Cartier, no credit card information was directly compromised as it was handled by a third-party processor. This incident highlights the widespread risk of password reuse and the need for stronger user authentication practices like multi-factor authentication (MFA).
Victoria’s Secret
In May 2025, lingerie brand Victoria’s Secret experienced a significant cyber incident that forced them to temporarily shut down corporate systems and their e-commerce website. The disruption also affected some in-store operations and led to a delay in their quarterly earnings report. While specific details on data compromise are less explicit in initial reports, the incident is suspected to be linked to a sophisticated cybercriminal group known as “Scattered Spider,” potentially involving the “DragonForce” ransomware. The primary impact here was operational disruption and potential financial repercussions due to system downtime, demonstrating how cyberattacks can cripple business continuity beyond just data theft.
Key takeaways
Drawing parallels with these recent incidents, several key lessons emerge for all businesses, especially those in the retail sector:
- No immunity for big brands: Even globally recognized and seemingly secure companies can be attractive targets. Cybercriminals are increasingly sophisticated and persistent, viewing extensive customer databases as lucrative assets.
- Evolving attack vectors: While ransomware and direct system infiltration remain prevalent, techniques like credential stuffing (The North Face) exploit common user behaviors and highlight the importance of unique, strong passwords and MFA. Social engineering tactics are also becoming more refined, often serving as initial entry points (potentially in the Victoria’s Secret case).
- The double extortion threat: Cybercriminals are increasingly employing double extortion, namely stealing data and encrypting systems to pressure victims. While not publicly confirmed for all these cases, it’s a growing trend that complicates incident response.
- Business continuity is paramount: Victoria’s Secret’s operational disruption underscores the critical need for comprehensive business continuity and cyber resilience plans. Minimizing downtime during and after an attack is essential to mitigate financial and reputational damage.
- Third-party risk management: Many breaches originate from vulnerabilities in third-party vendors or partners. Businesses must rigorously vet and monitor the security postures of their entire supply chain.
- Employee training and awareness: Human error remains a significant factor in successful cyberattacks. Continuous employee training on identifying phishing attempts, social engineering tactics, and the importance of strong security hygiene is crucial.
- Proactive investment in security: Beyond reactive measures, continuous investment in advanced security technologies, threat intelligence, and skilled cybersecurity personnel is no longer optional. This includes robust access controls, encryption, and regular security audits.
These cases are a powerful reminder that cybersecurity is not just an IT function, but it’s a core business imperative. Protecting digital assets, customer trust, and operational integrity demands a comprehensive, proactive, and continuously adapting security posture. Brands must move beyond simply reacting to breaches and embrace a culture of cyber resilience to safeguard their future in an increasingly perilous digital landscape.
What can you do about it?
As mentioned, even well-known big global brands can fall victim to cyber attacks that can severely disrupt business operations. Building stronger cyber resilience has now become a strategic imperative for organizations of all sizes, across every industry.
At Swiss Cyber Institute, we are committed to supporting companies in strengthening their defenses. One of our core offerings is Team Training, designed to embed security awareness and best practices across all levels of your organization. From entry-level employees to senior executives, our training programs are tailored to real-world scenarios and current threats. Our approach is grounded in globally recognized standards, including the NICE framework.
Secure your organization and strengthen resilience. Contact us to learn more.




![Recent Ransomware Attacks 2020 Explained [Part 1]](https://scf-5-sci-2025.hipdev.pro/wp-content/uploads/2021/04/Recent-Ransomware-Attacks-2020-Explained-scaled.jpg)


